Initiatives to Upgrade Information Security
To protect information assets from various threats and to fulfill its social mission, SCSK has established and is operating the Information Security Management System. We are continuously evaluating risks to information assets and ensuring the effectiveness of countermeasures for these risks. To ensure that each of our employee, as well as everyone that does business with SCSK, understands our Information Security Management System, including the Basic Policy, we engage in extensive educational activities, such as holding training courses on information security and the protection of personal information. We also require our subcontractors to adhere strictly to the Information Security Guidelines that we have established, and we are working to prevent occurrences of issues related to information security.
Furthermore, SCSK's data centers are ISO 27001 certificated, an international standard for information security management systems.
Management frameworks for information security
SCSK considers information security to be one of management’s top priorities. We have established the Chief Information Security Officer as the person in charge of building the information security structure and information security management system as well as the process for continual improvement.
In addition to the above, the Information Security Management Dept. has been established as an organization to aid the Chief Information Security Officer and manage and promote information security at SCSK.
The Information Security Management Dept., which is under the Chief Information Security Officer, takes the lead in increasing mutual collaboration among information security related departments and implementing information security measures across the entire company in unison with business groups.
Initiatives to strengthen information security
At SCSK, we have incorporated information security standards into SmartEpisode Plus (SE+), our standards for executing operations such as developing and operating systems.
To protect information assets that are the important assets of clients, we are also making information handled and risks visible, building a system to evaluate and improve security measures (S-SIMS*1), and continuing to undertake surveys and improvement activities covering 220 items and targeting all projects being undertaken, regardless of monetary amount or size.
As an IT business operator entrusted with the important information assets of clients, we will continue to improve engagement awareness and professional ethics through training for all employees.
*1 S-SIMS: SCSK Security Information Management System
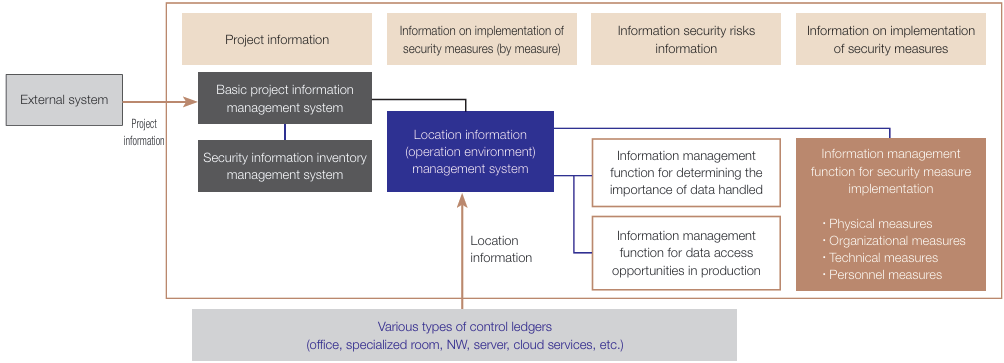
Summary of the SCSK Security Information Management System (S-SIMS)
This is a system for obtaining an integrated understanding of and making visible the information security risks and state of security measures for each project and running through the PDCA cycle for appropriate information management by collaborating with worksites and organization line levels.
Response to Cyber Security Incidents
SCSK-CSIRT*2 system
We have organized SCSK-CSIRT to ensure a prompt response and minimize damage should a computer security incident occur.
Aimed at appropriate incident response, departments in charge of internal information systems and departments responsible for cybersecurity work together to analyze incidents and discuss response policy and methods. They also work alongside external organizations, such as JPCERT/CC*3 and NISC.*4
By obtaining an accurate understanding of the situation through a prompt discussion with the relevant departments on compliance, legal matters, business impacts, and so forth, SCSK-CSIRT makes a speedy decision on a response based on the degree of impacts.
*2 SCSK-CSIRT (Computer Security Incident Response Team): A permanent organization that carries out activities in response to computer security incidents
*3 JPCERT/CC (Japan Computer Emergency Response Team Coordination Center)
*4 NISC (National center of Incident readiness and Strategy for Cybersecurity)
-
Responding to emergencies
- To minimize damage should an incident occur, SCSK-CSIRT has established rules on the structure and response procedures that enable speedy decisions on system shutdown and recovery.
-
Training and drills
- We provide all executives and employees with information security education using e-learning to prevent damage from cyberattacks.
- We conduct phishing email drills to prevent damage from targeted attacks.
- In addition, we are carrying out tabletop drills based on incident scenarios so that SCSK-CSIRT and related departments can collaborate smoothly and implement a swift response, etc.
-
Response to vulnerabilities
- We have established security countermeasure standards for servers and cloud services accessible from the Internet. We regularly assess their compliance with the standards while also checking and correcting their vulnerabilities.
SCSK-CSIRT System Diagram
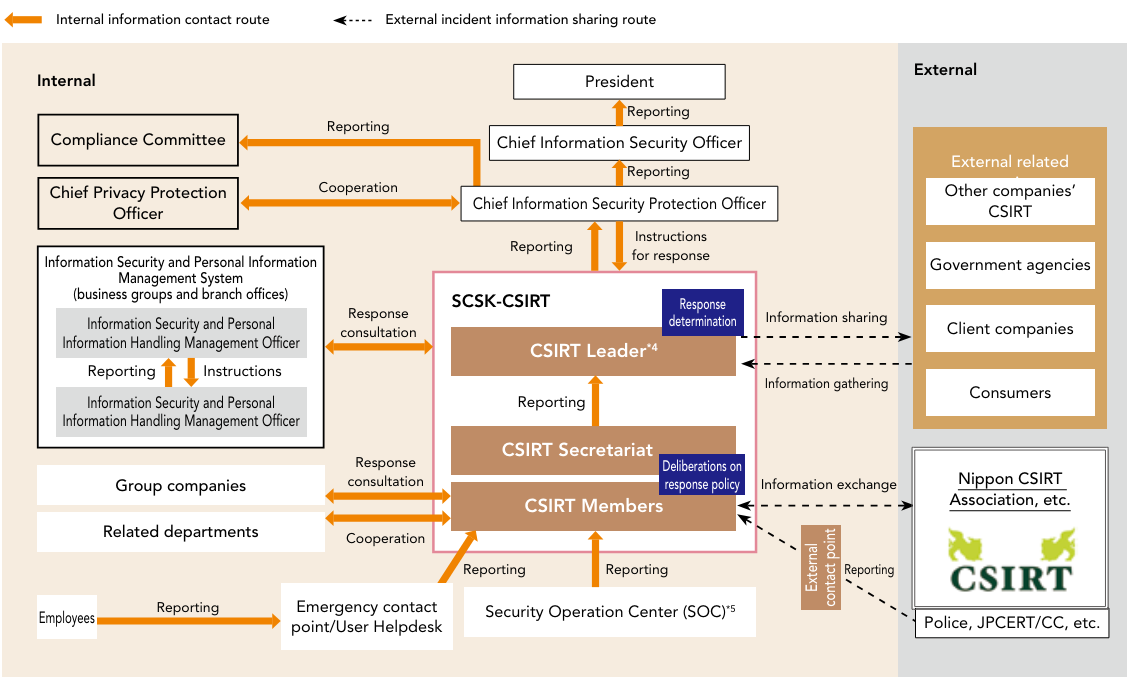
*5 The general manager of the department responsible for information security or center director serves as the leader. The current CSIRT Leader is the General Manager of the Corporate Information Systems Div.(as of April 2025)
*6 SCSK has built a CSIRT system to handle cybersecurity incidents, and constantly cooperates with the Security Operation Center (SOC), which is responsible for monitoring networks and devices, including SCSK in-house network.
